Published
Weekend Reading — That Emergency Chi-Squared Test

Galit Ariel "Because – Tuesday."
Design Objective
The Design Process of “Why Do Cats & Dogs ...?” A long and thorough read, exploring the visualization of related search terms.

Mitch Goldstein What about the prequels?
Graphic Designer
Product Designer
Interaction Designer
Web Designer
Digital Designer
UX Designer
Design: Ragnarok
Episode VII: The Designer Awakens
2 Graphic 2 Design
The Lord of the Fonts
Designers: Infinity War
The Designer Identity
Digital Designer & the Prisoner of Azkaban
Tools of the Trade
Up to 20% of your application dependencies may be unmaintained This number feels like it's on the low end, I venture to guess closer to 80%. But not the point. Tidelift's business model is selling maintenance contracts to businesses, and using that money to pay open source developers to maintain their codebase. Different from Gitpay. I hope both work out, and we find a sustainable model for open source development.
Matt Galligan It works! Maybe QR codes are useful after all …
First time seeing a QR code to join a guest WiFi network w/ a password at an office. Worked great on both my iPhone and iPad…had no idea this capability existed!
Found this generator for WiFi-specific QR code. Could be useful: www.qifi.org
Iconic consoles of the IBM System/360 mainframes, 55 years old As a child of the 70's, I find these top-of-the-line computers fascinating. Back then, massive boards with blinking lights were both science fiction, and the cutting edge. Also, Mythical Man-Month.

Web-end
Nathan Froyd I can't even …
"...the user agent string for the latest Dev Channel build of Microsoft Edge: "... Edg/74.1.96.24" We’ve selected the “Edg” token to avoid compatibility issues that may be caused by using the string “Edge,”..."
We are now deliberately misspelling words in the User-Agent string.
Rob Dodson Have you noticed it as well?
The thing about
position: stickyis that it only works in articles which explain how to useposition: sticky.
Lynn Fisher This thread full of awesome CSS looping videos …

Lingua Scripta
Jordan Scalesz "Friendly reminder that "o_o" is a valid identifier in JavaScript if you want little buddies to watch over your functions"

Architectural
Jeff Atwood True!
Of all the technical debt you can incur, the worst in my experience is bad names -- for database columns, variables, functions, etc. Fix those IMMEDIATELY before they metastasize all over your codebase and become extremely painful to fix later.. and they always do.
Software Maintenance, Understanding the 4 Types Not all software maintenance is the same, and it helps to know the difference:
Every time that you make changes to a software system, it is essential to identify the type of maintenance that you are performing. Keeping track of it gives excellent insights into your engineering practices. For example, the percentage of time that you spend in each of the four maintenance types gives you an idea of the maturity and skill level of your software engineering organization. It can also give you an idea of the maturity level of your product and codebase.

Reconciling GraphQL and Thrift at Airbnb So long REST, and thanks for all the fish.
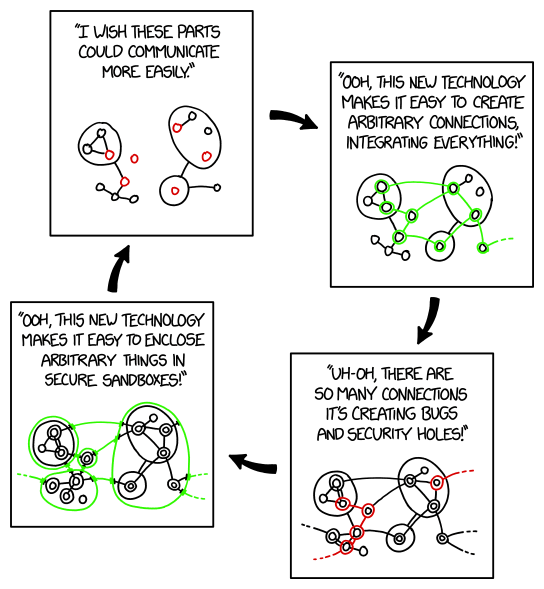
Vallery Lancey The infinite cycle:
XKCD "Sandboxing Cycle" is an evergreen slide when talking about abstraction layers.
It's not just security... abstractions are inherently leaky, which means sometimes you want to access the layers below, which voids many of the benefits of the abstraction.
Locked Doors
Colm MacCárthaigh Patching in production, a thread:
I think right around this minute is just about exactly 5 years since the Heartbleed vulnerability in OpenSSL became public. I remember the day vividly, and if you're interested, allow me to tell you about how the day, and the subsequent months, and years unfolded ...
Kevin2600 "Perfect Social engineer example. Happy hacking 🤓"

Facebook Boots 74 Cybercrime Groups From Platform This is what happens to your meme data:
Researchers said a simple search on Facebook for keywords like “spam,” “CVV” or more returned results for a slew of groups carrying out these illegal services. In total, the groups had approximately 385,000 members – and some had been up on Facebook for as long as eight years, researchers said.
And, of course, the algorithm:
Ironically, when researchers joined some of these groups, Facebook’s algorithm suggested that they join other groups promoting illicit activity under its “Suggested Pages” tab.

Evan Osnos Lovely security "feature" in older iOS:
Uh, this looks fake but, alas, it’s our iPad today after 3-year-old tried (repeatedly) to unlock. Ideas?

None of the Above
Nature News & Comment "Dr. Katie Bouman, who led the creation of an algorithm that helped capture the first ever image of a black hole, tells us what this breakthrough means for science 👩🔬 #EHTBlackHole #BlackHole"
How to make sense of the black hole image We have turned the entire Earth into one giant telescope!
Ronan Farrow "Ah yes, the classic homeowner’s problem of checks notes bees paying off your mortgage."

What happened when Oslo decided to make its downtown basically car-free? Don't worry. It turned out for the best.
A couple of decades ago, it was perfectly normal to smoke cigarettes inside. Today, very few would do that. I think it’s the same with cars in the city center: One day we will look back and ask ourselves why we ever thought that was a good idea.

Shockingly Good Smartphones You Can Get for $350 or Less Let that video be a cautionary tale about removing your phone battery.

Luuuda You can never be too prepared:
A couple years ago in central park I saw a lady on her phone looking panicked and I overheard her say “ok what we need to do is run a chi-squared test immediately!”
I still think about that emergency chi-squared test
Ana Oppenheim "My German might be very basic but this headline is hard to disagree with"

Seth Masket "Oh, honey."
The Hill Switzerland's highest court overturns referendum for first time ever after finding voters were poorly informed
The Guardian’s nifty old-article trick is a reminder of how news organizations can use metadata to limit misinformation Simple tech tricks that can help combat misinformation.

The key to glorifying a questionable diet? Be a tech bro and call it ‘biohacking.’ Not mincing words:
It's fascinating to watch the language of food consumption mutate as it travels across genders. For decades, "dieting" was the domain of women. It looked like Weight Watchers, it looked like Snackwells, it looked like South Beach, but whatever it looked like, it was always portrayed as something simultaneously necessary, shameful, pride-inducing, hated and ever-present.
The term became a victim of “gender contamination,” as Amanda Mull wrote in the Atlantic — which is “when a product or idea becomes so female-coded that men are no longer willing to engage with it.”
Instead men — and the companies that cater to them — found new ways to describe food restriction. Not “weight loss” but “performance-enhancing.” Not “look great” but “perform better.”
Mashable "These sculptures are not what they seem"
