Published
Weekend Reading — Exponential growth

Duck Wearing Bow-Tie Walks Into Pub, Drinks Pint, Fights Dog, Loses
This week we say goodbye to mixed content; dance like
ᕕ(⌐■_■)ᕗ ♪♬; we troll ES5 developers; we take a hike and fix a bug; we play murder mystery; we decide ethics in programming is a thing; 5 reasons we don't answer your phone calls; we wonder, would god troll?
Design Objective
Chrome finally kills off the HTTP-HTTPS “mixed content” warning Perfect example of the relationship between security and usability:
The problem is that it's almost impossible to switch completely from HTTP to HTTPS in one fell swoop—there are just too many factors that need to be tested and debugged. At the same time, webmasters weren't keen to begin the migration process to HTTPS because of that pesky mixed content warning, which had a tendency to spook less-experienced users of the Information Superhighway.
Tools of the Trade
Web pages with unscalable viewports shouldn't have a single tap delay Safari on iOS is losing the 300ms tap delay, but only when viewport is unscalable. Some webapps would feel like native apps, and I hope that's the trend.
Node.js Security Checklist A checklist to guides you through must have security checks before deploying your application, courtesy of RisingStack.
smartcrop.js Content aware image cropping.
And so it begins - just spent an hour debugging "website is blank" complains. Turns out ios9 content blockers are blocking legit content
IronFleet: Proving Practical Distributed Systems Correct (PDF)
This paper presents IronFleet, the first methodology for automated machine-checked verification of the safety and liveness of non-trivial distributed system implementations. The IronFleet methodology is practical: it supports complex, feature-rich implementations with reasonable performance and a tolerable proof burden.
IBM cuts down IT support staff w/ Mac deployment, says 5% of Mac users call help desk vs 40% for PCs That's the same IBM that was synonymous with PCs for the past 34 years:
Previn noted that “Every Mac that we buy is making and saving IBM money,” and that “A Mac still has value three or four years down the road.”
Asky ASCII Art as a Service ᕕ(⌐■_■)ᕗ ♪♬
Foolish Solutions for Bloat Maciej Cegłowski recreates Google's AMP promotion page, only better (more details):
The following publishers have joined the Accelerated Mobile Pages Project instead of just fixing their websites.
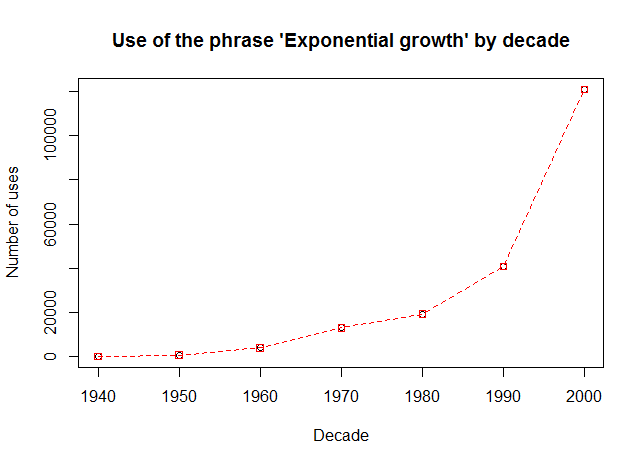
@mc_hankins "Use of the phrase 'exponential growth' by decade"
Lingua Scripta
How to Use Classes and Sleep at Night There's nothing wrong with classes in JavaScript, but we should learn from Java and not repeat the same old mistakes. This is a fairly good policy:
- Resist making classes your public API.
- Don’t inherit more than once.
- Don’t make super calls from methods.
- Don’t expect people to use your classes.
- Learn functional programming.
#NodeJS : A quick optimization advice In V8 you can make code run faster by … removing some comments …
Node v4.2.0 (LTS) The first release under the new LTS plan: "support for v4.x will continue for a period of 30 months from today."
I'm going to use this code sometime just to troll coworkers.
const two = 2; const one = 1; if (one => two) { alert('whoops!'); }```
Mancy JavaScript REPL as a standalone (Electron) application.
ES6 in WebKit Safari in iOS 9 and OS X 10.11 supports classes, promises, new collections, symbols and few other ES6 features.
Template literals are strictly better than quoted strings
- Multiline
- Interpolation
- Text rarely has ` in it
Lines of Code
@drwave The secret to killing it as software developer, in a nutshell:
In order to fix that bug I had to:
- have a good night’s sleep
- take a 2 hour hike
and then write one line of code.
Question to consider when choosing a programming language: Do I want to become like the people who use this language?
a tale of software maintenance: OpenSSL and EVP_CHECK_DES_KEY I think OpenSSL has a serious affliction of code hoarding.
This coffee shop is so crowded I accidentally fixed a bug in someone else's code base.
@shinypb "Pair programming."
Architectural
The Seven Deadly Sins of Microservices (Full Version) Fantastic presentation on the pits and traps of microservices. Also this gem:
"I will postpone using this shiny new framework until my peers have validated the proposed benefits with rigorous scientific experiments"
-- Said by no programmer … ever
We replaced our monolith with micro services so that every outage could be more like a murder mystery.
Ethically Speaking
An Engineering Theory of the Volkswagen Scandal
Indeed, it was hard to believe. A couple of rogue engineers took it upon themselves to write and install software that slashed emissions on Volkswagen diesels, but only when the cars were being tested, then kept it from senior company figures?
Hard to believe it was a rogue engineer, and not a systematic process. But then, does it really matter? Time we come to terms with …
Since we will be blamed in any case, the burden of software ethics is upon us, the programmers.
Secret source code pronounces you guilty as charged
She said that she has the right to confront the evidence being used against her client. "When you put data into computer and it spits out something, you'd like to know how it did it."
Technotopia
If video games have taught me anything, this cat has a side quest to offer me.
Peopleware
Why I don’t answer most phone calls
Unfortunately, this immediateness increases the chance of the caller to thinking out loud, because he didn’t take the time to think before reaching out to the callee. I sometimes end up listening to a verbose and unclear phone call, or even an irrelevant one.
Things men have actually said to me at tech events And check the comments to see how many men think this is acceptable behavior.
This should totally be a thing. gm;np
(Goalpost moved; not playing)
Man tries to put out garbage fire by driving over it in a van loaded with ammunition Hoomans.
Locked Doors
Cops Don’t Need a Crypto Backdoor to Get Into Your iPhone All the ways in which anyone can access data on your phone.
Why is length > complexity? Because math... On choosing passwords that are hard to crack.
How is NSA breaking so much crypto?
For the most common strength of Diffie-Hellman (1024 bits), it would cost a few hundred million dollars to build a machine, based on special purpose hardware, that would be able to crack one Diffie-Hellman prime every year.
None of the Above
Went to Niels Bohr's grave today, and some wag put dice on it. #wellplayed
Computer science is now the top major for women at Stanford University
Based on preliminary declarations by upper-class students, about 214 women are majoring in computer science, accounting for about 30 percent of majors in that department, the California-based university told Reuters on Friday.
The Elephant in the Room and follow up Unpacking the lie that is "I'm not doing anything that you can't do", see also 37 Signals, Radiohead, et al:
The idea that any app developer can witness Marco's attempt at a different business model, and employ the idea in their own app offering, is true. Anybody can try this model if they wish, the difference is that hardly any other developers will.
“Hi, I’d like to add you to my professional network on LinkedIn”



