Published
Weekend Reading — Do dates make you nervous?
Design Objective
Design Better Data Tables How to display tabular data:
Tables might be boring, but they are such a major element of any data-rich document that they’re worth every ounce of design thinking we can apply to them.
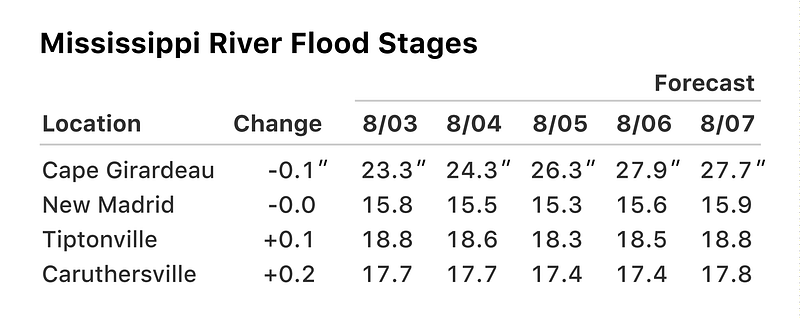
Just as title case looks more formal and serious, sentence case looks more casual and friendly.
I beg to differ. In the age of conversational UI, casual and friendly is expressed in all lower case. Sentence case is for formal and serious. Also, bots.
Introducing BuzzFeed’s Design Process Combining design phases with feedback loops and iterations:
It’s not uncommon for inexperienced designers to jump to solutions before they’ve fully unpacked and understood a problem, or to fold in all feedback they’ve received because “my peers are smart” without practicing the skill of filtering out input that’s distracting or not inline with the goals of a project.
Peek Inside a Facebook Design Critique "By showing how design critiques at Facebook typically go, we wanted to highlight what makes for a good critique and what can often get in the way."
Hidden Expectations The hardest parts of the Web are the invisible parts: accessibility, security, performance, and empathy.
The Headless Web Makes the strong case for a future of the web, which is not exclusive to web browsers:
If we can provide a world where content and utility on that content are available headlessly then I think we are in a good position.
Tools of the Trade
This Image is Also an HTML Webpage Cool trick.
The performance benefits of rel=noopener In addition to the privacy benefits.
attic-labs/noms A decentralized database based on ideas from Git. If you ever wanted a database that can do versioning, forking and merging, quick reverts.
Haka Software defined security:
The scope of Haka language is twofold. First of all, it allows to write security rules in order to filter/alter/drop unwanted packets and log and report malicious activities. Second, Haka features a grammar enabling to specify network protocols and their underlying state machine.
2004: rake -T
2009: bundle exec rake -T
2014: foreman run bundle exec rake -T
2016: docker run -d -p 3000:3000 --nafuuu ... (╯°□°)╯︵ ┻━┻
Friend: Do dates make you nervous?
Me: omg yes especially when doing math across timezone boundaries
@jessicard "web dev is fucking brutal"

Lingua Scripta
ECMAScript proposal updates @ 2016-07 All the stuff that's destined for ES2017. Glad to see async/await made the cut.
TIL JavaScript has a special 'long arrow' syntax to iterate over a range of numbers
let i = 10;
while (i --> 0) {
console.log(i);
}
Huge number of files generated for every AngularJS 2 project First step is admitting you have a problem:

Lines of Code
How To Write Unmaintainable Code A classic.
DearDevelopersWhiteSpaceIsFreeSoFeelWelcomeToUseAsMuchOfItAsYouWantMOFOS
OH: "Can you give me an estimate on how long it will take you to fix this bug?"
"That's like asking how long it will take to find my keys."
Programming is like
- Get 68 people to write a book
- Simultaneously
- End is sort of vague
- Change the topic twice
- Pedantic people
- Lots of Coffee
Architectural
Notes on concurrency bugs Through the eyes of academic literature on non-deterministic bugs:
97% of examined deadlock bugs were caused by two threads waiting for at most two resources
Moreover, 22% of examined deadlock bugs were caused by a thread acquiring a resource held by the thread itself.
"by simply dropping two pizzas into any organisation, teams will form around them, and then you have devops" - @phillip_webb #s1p @pivotal
@assaf "WontFix: feature delivered exactly as specced"

Peopleware
We assume that everything we have once written is visible to every newcomer. Nope. Repeating the best practices should be a best practice.
Locked Doors
In a snakeoil presentation I heard: "you should use foxit, everyone has an Adobe Reader 0day", so I tried to find a bug in foxit,it was easy
New attack steals SSNs, e-mail addresses, and more from HTTPS pages Sky not falling, but this is a very interesting technique:
To determine the size of an HTTPS-protected response, the attacker uses an oracle technique that returns what amounts to a yes-or-no response to each guess. When a request containing "value=" results in the same data size, the attacker knows that string is inside the encrypted response and then tries to modify the guess to include the next character, say "value=0".
Sensible Privacy: How We Can Protect Domestic Violence Survivors Without Facilitating Misuse When the main potential attackers are the survivor's partner.
So I accidentally broke a Skype messaging bot..

None of the Above

The Oppressive Gospel of ‘Minimalism’
Today’s minimalism, by contrast, is visually oppressive; it comes with an inherent pressure to conform to its precepts. ... It is anxiety-inducing in a manner indistinguishable from other forms of consumerism, not revolutionary at all. Do I own the right things? Have I jettisoned enough of the wrong ones?
Dogs Are Being Used To Explain Body Positivity To Children, And It’s Pretty Great

IBM creates world’s first artificial phase-change neurons "They behave like biological neurons, including low power usage and dense scaling."
Specialized fires up color-changing, heat-sensitive paint for Olympians "The Torch paint transitions from a deep red to bright yellow as the temperature rises above 71ºF (22ºC)" Want!

I Replaced The Word ‘Millennials’ With ‘43-Year-Old White Men’ Haha.
Primitive Technology: Forge Blower Using sticks and clay to build a forge blower to make iron:
