Published
Weekend Reading — Codependent watches
Design Objective
Best #1 design tip: close eyes; take breath; clear mind; open eyes. Now pretend you're a human being who has to read/use/do this. Simple.
Single Responsibility Designing better CSS by following the single responsibility principle.
Das Referenz: Wikipedia Redesigned for iPad It's a fabulous app, try it out. It's also how you do a redesign: not with images, but with working prototypes.
Why and How to avoid Hamburger Menus Hamburgers are food.
Just because it's low-tech doesn't mean it's not cool

Tools of the Trade
jsonwatch works like watch -d but with JSON documents.
Shuttle A simple SSH shortcut menu for OS X.
Notifyr Receive iOS notifications on your Mac. Not sure if that's a Good Thing™.
MQTT and Node.js Quick introduction to MQTT, a lightweight pub/sub protocol, designed specifically for working with low power devices (IoT).
lovell/sharp Fast Node image resizing, similar API to GraphicsMagick but claims to be 8x faster.
VisualOps A visual tool for designing and managing AWS stacks. What You See Is What You Deploy?
codeanywhere A code editor you can use in the browser, with mobile apps for iOS, Androids. This is the first I've seen that also supports Github (everything else uses … wait for it … FTP).
Lines of Code
Components Should Be Focused, Independent, Reusable, Small & Testable (FIRST):
the secret to efficiently building ‘large’ things is generally to avoid building them in the first place. Instead, compose your large thing out of smaller, more focused pieces.
Correct Erlang usage mandates you do not write any kind of defensive code. This is called intentional programming. You write code for the intentional control flow path which you expect the code to take
Locked Doors
The eBay breach: answers to the questions that will inevitably be asked TL;DR your data has been leaked, took eBay several months to find out; it may be hashed, or encrypted (reversible). Given that they restrict password length and disable pasting, I wouldn't be surprised if they didn't hash.
How I bypassed 2-Factor-Authentication on Google, Facebook, Yahoo, LinkedIn, and many others. TL;DR any service that sends a code/pin to your phone is insecure by design.
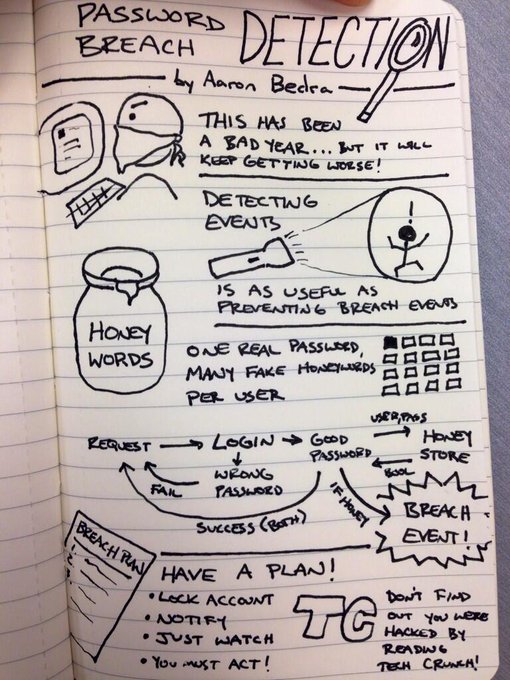
Honey words Cool trick:
None of the Above
brettapproved Accessibility ratings for restaurants, hotels and entertainment venues.
Meet the electric motorcycle that's now the fastest production bike in the world

 "Smart" watches 1982 vs 2014
"Smart" watches 1982 vs 2014